11![An (Almost) Constant-Effort Solution-Verification Proof-of-Work Protocol based on Merkle Trees (extended and colored version of [7]) Fabien Coelho ´ CRI, Ecole des mines de Paris, An (Almost) Constant-Effort Solution-Verification Proof-of-Work Protocol based on Merkle Trees (extended and colored version of [7]) Fabien Coelho ´ CRI, Ecole des mines de Paris,](https://www.pdfsearch.io/img/619596a3b4d8747399ee22fb59c93e35.jpg) | Add to Reading ListSource URL: hashcash.orgLanguage: English - Date: 2008-06-22 07:14:34
|
|---|
12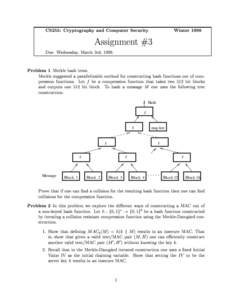 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 1999-02-22 15:26:53
|
|---|
13 | Add to Reading ListSource URL: www.cs.cornell.eduLanguage: English - Date: 2005-03-20 00:13:33
|
|---|
14 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2005-01-04 13:22:38
|
|---|
15 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2004-03-10 16:54:18
|
|---|
16 | Add to Reading ListSource URL: web.mit.eduLanguage: English - Date: 2011-05-17 23:49:49
|
|---|
17 | Add to Reading ListSource URL: crypto.stanford.eduLanguage: English - Date: 2006-01-11 14:38:17
|
|---|
18![Extendable-Output Functions (XOFs) Ray Perlner Computer Security Division, NIST [removed] SHA[removed]Workshop Extendable-Output Functions (XOFs) Ray Perlner Computer Security Division, NIST [removed] SHA[removed]Workshop](https://www.pdfsearch.io/img/0878689fdc1958749402151e095d599c.jpg) | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2014-08-22 14:11:38
|
|---|
19 | Add to Reading ListSource URL: www.iacr.orgLanguage: English - Date: 2008-09-15 00:54:54
|
|---|
20 | Add to Reading ListSource URL: eprint.iacr.orgLanguage: English - Date: 2014-09-03 05:03:49
|
|---|